 The largest DDoS attack ever disclosed slammed into the servers of software development site GitHub at 17:21 UTC last Wednesday, hitting a peak of 1350 gigabits per second with a follow-up reaching 400 gigabits per second. The attack exploited amplification, a technique we’ve seen before in previous mega DDoS incidents but this time hitting a target called Memcached. Memcached is a popular technology designed to provide free & open source, high-performance, distributed memory object caching system, generic in nature, but intended for use in speeding up dynamic web applications by alleviating database load. Memcached is simple yet powerful. Its simple design promotes quick deployment, ease of development, and solves many problems facing large data caches. Its API is available for most popular languages. By default, it allows unauthenticated external connections on UDP port 11211, which means the attackers were able to generate large amounts of traffic simply by sending servers left in this weak state a simple “stats” command from a spoofed IP address.
The largest DDoS attack ever disclosed slammed into the servers of software development site GitHub at 17:21 UTC last Wednesday, hitting a peak of 1350 gigabits per second with a follow-up reaching 400 gigabits per second. The attack exploited amplification, a technique we’ve seen before in previous mega DDoS incidents but this time hitting a target called Memcached. Memcached is a popular technology designed to provide free & open source, high-performance, distributed memory object caching system, generic in nature, but intended for use in speeding up dynamic web applications by alleviating database load. Memcached is simple yet powerful. Its simple design promotes quick deployment, ease of development, and solves many problems facing large data caches. Its API is available for most popular languages. By default, it allows unauthenticated external connections on UDP port 11211, which means the attackers were able to generate large amounts of traffic simply by sending servers left in this weak state a simple “stats” command from a spoofed IP address.
This compares favorably with previous amplification attacks such as the 2013 DNS-themed assault on Spamhaus, which boosted responses 50 times to 300 gigabits per second peak. Then later it was the NTP protocol that was abused in a 400 gigabits per second attack on French hosting company OVH that exploited an amplification rate of 500 times. The mitigation companies must have have suspected something unpleasant , which is why Akamai’s Prolexic division shut it down so rapidly. Luckily, it’s not that hard to stop using perimeter firewalls to block UDP on the named port or disabling UDP on Memcached servers altogether. The underlying problem here is once again poorly-secured infrastructure – estimates of the number of vulnerable Memcached servers range up to around 95,000, with almost all being in the US and China.
Someone will now have to persuade the owners of all those vulnerable Memcached servers to close the vulnerability or risk intervention by large ISPs. Perhaps this time the attackers were testing out a new idea because it has even been suggested that it was a ransom attack because there appeared to be an embedded demand for the Monero virtual currency.
 DDoS attacks come in many different forms, from Smurfs to Teardrops, to Pings of Death. Attackers build networks of infected computers, known as ‘botnets’, by spreading malicious software through emails, websites and social media. Once infected, these machines can be controlled remotely, without their owners’ knowledge, and used like an army to launch an attack against any target. Some attacks are so big they can max out a country’s international cable capacity. Botnets can generate huge floods of traffic to overwhelm a target. These floods can be generated in multiple ways, such as sending more connection requests than a server can handle, or having computers send the victim huge amounts of random data to use up the target’s bandwidth. These attacks sometime attempt to use up all the available connections to infrastructure devices such as load-balancers, firewalls and application servers. Even devices capable of maintaining state on millions of connections can be taken down by these attacks or even sometime overwhelm a specific aspect of an application or service and can be effective even with very few attacking machines generating a low traffic rate.
DDoS attacks come in many different forms, from Smurfs to Teardrops, to Pings of Death. Attackers build networks of infected computers, known as ‘botnets’, by spreading malicious software through emails, websites and social media. Once infected, these machines can be controlled remotely, without their owners’ knowledge, and used like an army to launch an attack against any target. Some attacks are so big they can max out a country’s international cable capacity. Botnets can generate huge floods of traffic to overwhelm a target. These floods can be generated in multiple ways, such as sending more connection requests than a server can handle, or having computers send the victim huge amounts of random data to use up the target’s bandwidth. These attacks sometime attempt to use up all the available connections to infrastructure devices such as load-balancers, firewalls and application servers. Even devices capable of maintaining state on millions of connections can be taken down by these attacks or even sometime overwhelm a specific aspect of an application or service and can be effective even with very few attacking machines generating a low traffic rate.
How DDoS amplification attact work on Memcached servers.
To understand the attack we much learn how Memcached functions in high-performance environment. Memcached is a general-purpose distributed memory caching system. It is often used to speed up dynamic database-driven websites by caching data and objects in RAM to reduce the number of times an external data source, such as a database or API, must be read. Memcached’s APIs provide a very large hash table distributed across multiple machines. When the table is full, subsequent inserts cause older data to be purged in least recently used order.Applications using Memcached typically layer requests and additions into RAM before falling back on a slower backing store, such as a database.
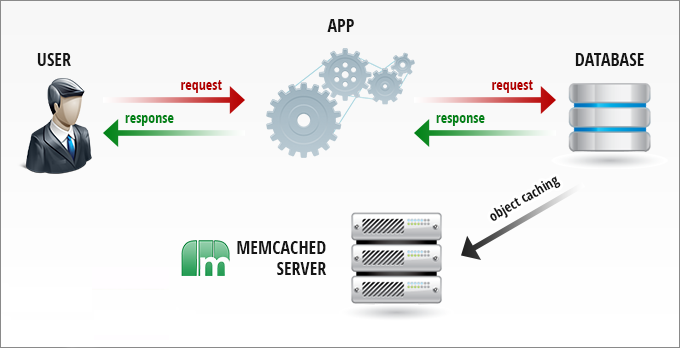
Just like any other amplification methods in which hackers send a small request from a fake IP address to get a much broader Memcache instead, the reinforcement attack response also works by sending a request to the target server port 11211 using fake IP address that matches the victim’s IP address. Only few bytes of request sent to vulnerable server can trigger ten thousands of times the resposne. The majority of Memcached servers are exposed to overuse of reinforcement.
Some research also says that the Memcached primitive queries used in these attacks can also be routed through TCP port 11211 on incorrect Memcached servers. TCP is not currently considered as high risk Memcached reflection vector because TCP queries cannot be falsified in a relaible manner. Even though the attack can be easily detected just by setting a rule on UDP traffic on source port 11211, it cannot be mitigated without a dedicated DDoS mitigation solution due to the massive amounts of packets per second (bits per second) delivered on this kind of attack. Massive traffic like this is likely to turn edge routing devices unavailable before real traffic arrives at the server, regardless of its configuration.
Jerika Inc. customers are protected against all known DDoS amplification attacks, and as of now they are protected against this specific attack as well.

That’s interesting web for me..
I added your web into my favourites!
P.S.: Looking forward for future updates!
Matthew
Attractive part of content. I simply stumbled upon your site and in accession capital to say that I acquire actually loved account your blog
posts. Anyway I will be subscribing in your augment or even I fulfillment you get entry to persistently fast.
I am genuinely grateful to the owner of this web page who has shared this wonderful
article at at this place.
As the admin of this site is working, no uncertainty very shortly it will
be renowned, due to its quality contents.
In some other cases, the PC main system breaks as a result of an internal error and you can’t access your data.
As most with the internet sites are carrying their financial transactions and
also information through internet and other electronic media, the increase of hacking and internet-based theft in addition has increased.
Anyway, perhaps you understand that feeling when hours pass 1 by 1 so you are overlooking them.
Hi, the whole thing is going sound here and ofcourse every one is sharing information, that’s actually good, keep up writing.
I don’t even know how I ended up here, but I thought this post
was good. I do not know who you are but certainly you’re going to a famous blogger if you are not already 😉 Cheers!
Does your blog have a contact page? I’m having trouble locating it but,
I’d like to shoot you an e-mail. I’ve got some creative ideas for your blog you might be interested in hearing.
Either way, great site and I look forward to seeing it expand over time.
Very quickly this website will be famous amid all blogging people, due to it’s pleasant content
Helpful info. Fortunate me I discovered your website unintentionally, and
I’m shocked why this coincidence didn’t happened
earlier! I bookmarked it.
I think the admin of this website is really working hard in support of his web
page, for the reason that here every data is quality based stuff.
I read this paragraph completely concerning the resemblance
of newest and preceding technologies, it’s remarkable article.
Hello are using WordPress for your blog platform? I’m new to the blog world but I’m trying to get started and create my own. Do you need any
html coding knowledge to make your own blog? Any help would be really appreciated!
Thanks in support of sharing such a good opinion, piece
of writing is pleasant, thats why i have read it entirely
I’m curious to find out what blog platform you’re
working with? I’m experiencing some minor security issues with my latest blog and I’d like to
find something more risk-free. Do you have any recommendations?
Have you ever considered creating an e-book or guest authoring on other sites?
I have a blog centered on the same subjects you discuss and would really like to have you
share some stories/information. I know my subscribers would enjoy your work.
If you are even remotely interested, feel free to shoot me
an e-mail.
I am truly delighted to glance at this weblog posts which carries
tons of helpful data, thanks for providing these kinds of information.
I’m amazed, I have to admit. Seldom do I come
across a blog that’s both educative and interesting, and let
me tell you, you’ve hit the nail on the head. The problem is something
not enough men and women are speaking intelligently about.
I am very happy I found this during my search for something relating
to this.
Great blog here! Also your web site loads up very fast!
What web host are you using? Can I get your affiliate link to your host?
I wish my site loaded up as quickly as yours lol
Hey! I could have sworn I’ve been to this site before but after checking through some of the post I realized it’s
new to me. Anyways, I’m definitely glad I found it and
I’ll be bookmarking and checking back often!
Keep on writing, great job!
What’s Happening i am new to this, I stumbled upon this I have found It positively useful and
it has aided me out loads. I’m hoping to give a contribution & assist different users like its aided me.
Great job.
Passion the website– very user friendly and great deals to see!
You should be a part of a contest for one of the best websites on the internet.
I will recommend this web site!
Pretty! This has been a really wonderful article.
Thanks for providing this info.
After exploring a few of the blog articles on your website,
I honestly like your way of writing a blog. I saved as a favorite it
to my bookmark site list and will be checking back
in the near future. Please check out my website as well and let me know how you feel.